Organizations are facing the increased risk of cyber-attacks, irrespective of size or industry.
In the last few years many malwares, ransomwares and vulnerabilities were discovered that affected many organizations. Known as Wannacry, Petya, Meltdown and Spectre. Wannacry exploited windows SMB, Petya exploited the Master Boot Record and the Meltdown and Spectre exploit critical vulnerabilities in modern processors. These hardware vulnerabilities allow programs to steal data which is currently processed on the compute.
These kinds of vulnerabilities allow attackers to access IT systems and applications, so it is essential for enterprises to verify and remediate weaknesses before they are exploited. A comprehensive penetration test can help companies improve the security posture of their systems. It can help to test an organization’s security policy compliance, its employees’ security awareness and the organization’s ability to identify and respond to security incidents.
This is where RADKRICS experts can help you by leveraging their expertise.
Penetration Testing is an attempt to evaluate the security of a Target (an IT application or infrastructure) by attempting to discover and exploit vulnerabilities. These vulnerabilities may exist in operating systems, services, applications, misconfigurations or end-user behavior. Such assessments are also useful in validating the efficacy of defensive mechanisms and end-user adherence to security policies or training.
Penetration tests are a combination of automated and targeted attacks with three levels of maturity of attack:-
Basic where automated tools are run,
Standard where the basic attacks are followed by exploits directly at discovered weaknesses
Advanced where zero day exploits are developed specifically against the Target.
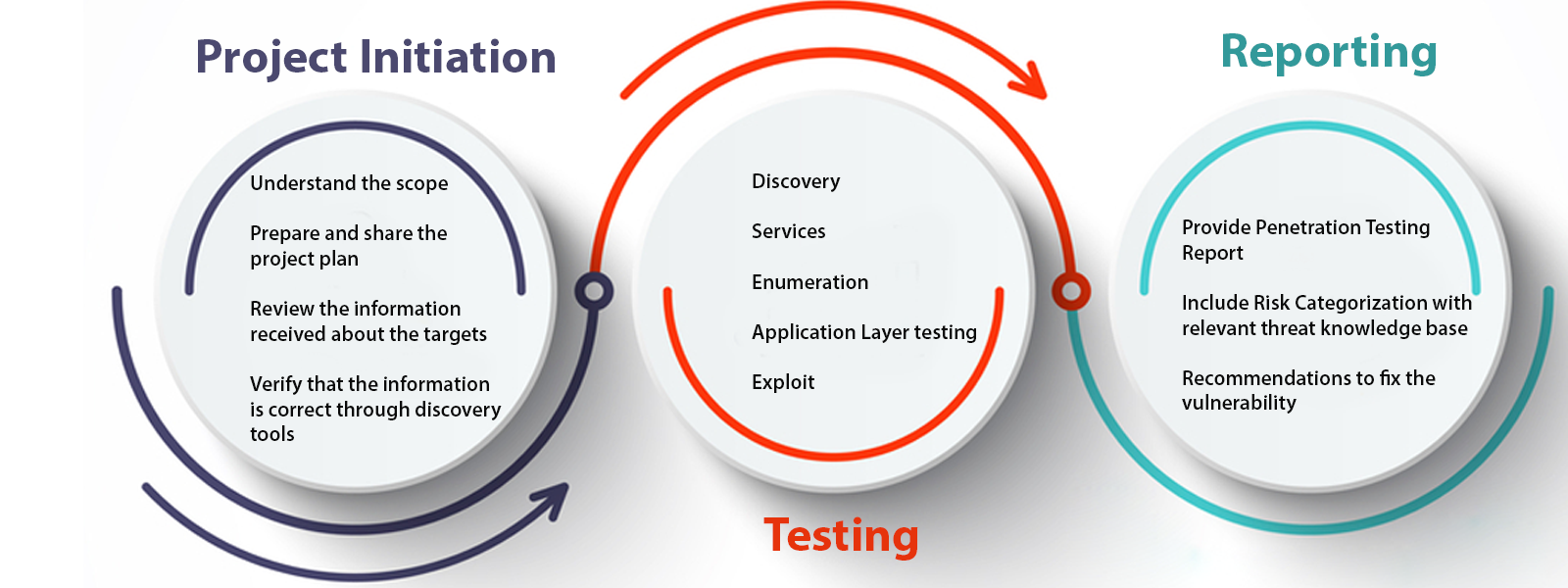
The process includes gathering information about the target before the test, identifying possible entry points, attempting to break in (either virtually or for real) and reporting the findings.
Information about security vulnerabilities successfully exploited through penetration testing is typically aggregated and presented to IT and network system managers to help those professionals make strategic conclusions and prioritize related remediation efforts.
Nessus
NMAP
Metasploit
Burp Suite
Kali
Plus open source tools